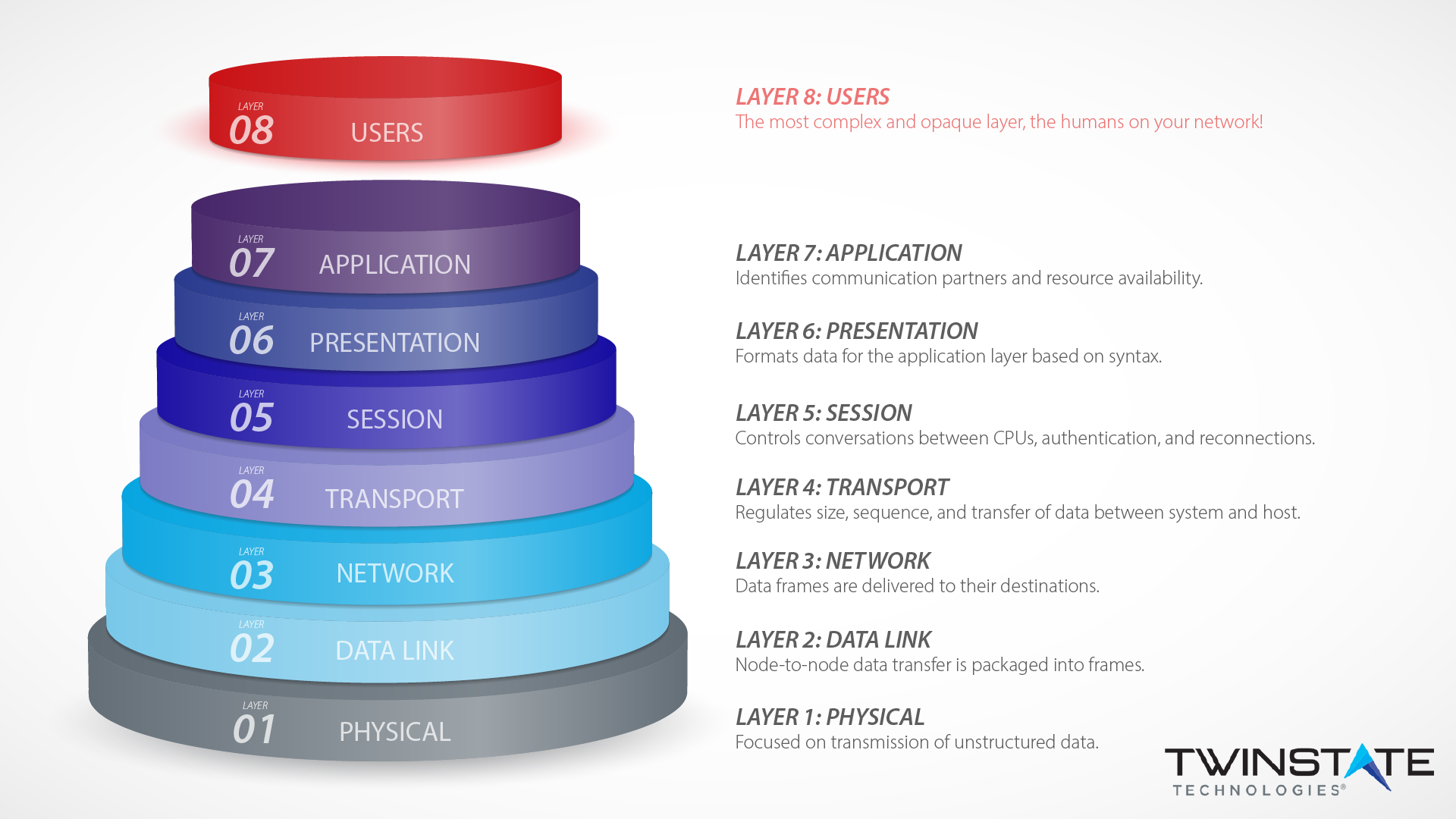
Layer eight security depends on end-users according to the OSI model. Learn how Twinstate Technologies protects the users at our Plattsburgh, NY office.

Patient Portal - Hudson Headwaters Health Network

BETA Technologies to launch major expansion in Plattsburgh

LayerEight

From Day One September Virtual: New Ideas for Successful

Packaging World May 2023 by PMMIMediaGroup - Issuu
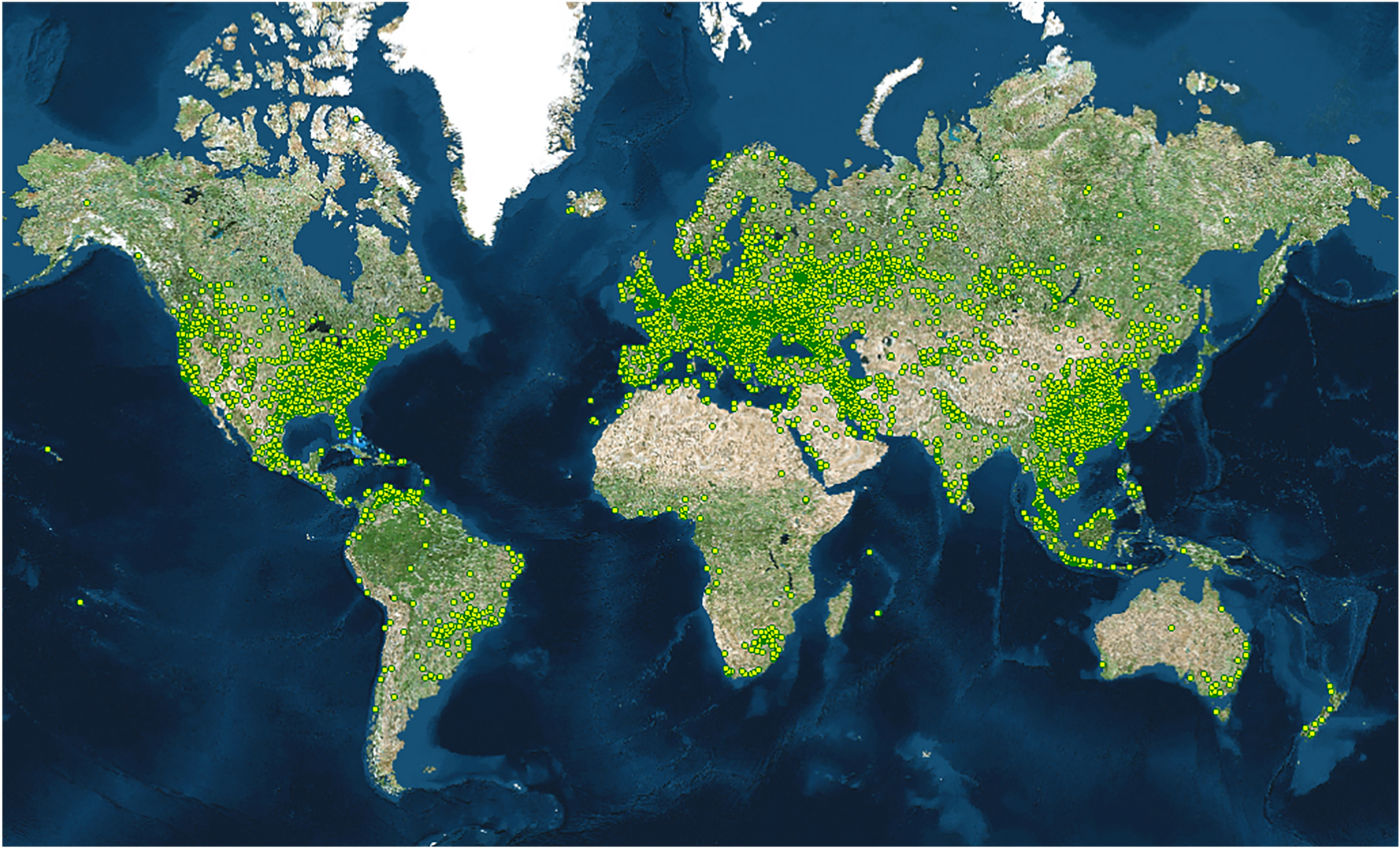
Spatial analysis of global Bitcoin mining
All-Inclusive, Fully Outsourced IT Management
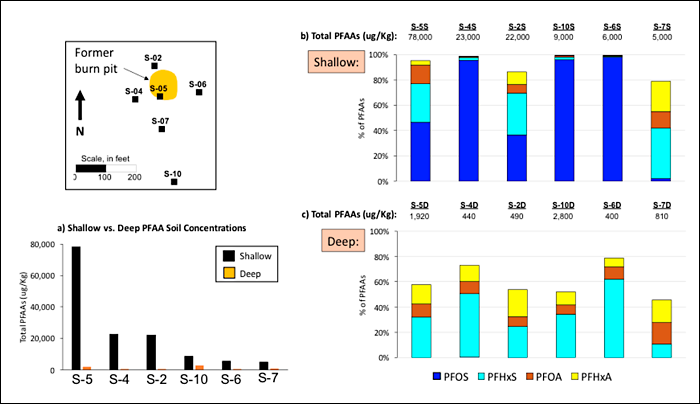
15 Case Studies – PFAS — Per- and Polyfluoroalkyl Substances
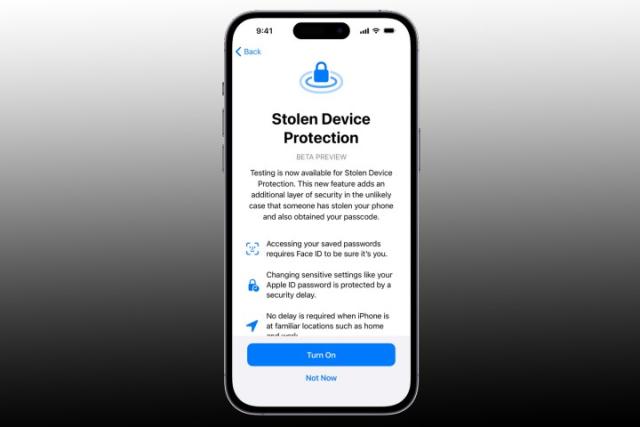
iOS 17.3 will give your iPhone a much-needed security upgrade
:format(jpg)/cloudfront-us-east-1.images.arcpublishing.com/coindesk/FXE72TIZBFG5VGGZR74HFC6JF4.png)
What Is Cryptojacking? How to Protect Yourself Against Crypto

PDF) Meta-Analysis of Big Data Security and Privacy Scholarly

Sustainability, Free Full-Text